PRODAFT Reports On the Inner Workings of the Notorious Ransomware PYSA Gang
Yverdon-les-Bains, Switzerland – Cybersecurity analyst firm PRODAFT has revealed the inner workings of a notorious hacking group, The PYSA Ransomware Group’s tool became notorious across 2020-21 as they focused on intruding into the IT systems of government agencies, educational institutions, and healthcare companies.
Unlike high-volume automated or massive denial of service attacks, the creators of PYSA carefully researched high-value and high-profile targets before launching an attack. PYSA stands for “Protect Your System Amigo,” part of the message shown to hacked organizations.
By compromising enterprise systems and encrypting key files, the PYSA group forced organizations to pay large ransoms to restore their data. PSYA is listed as an advanced ransomware group, carrying out its operations largely off the radar, but PRODAFT gained full visibility of the inner workings of the group.
See PRODAFT’s public report (PDF, no sign up required) for technical analysis of the group, investigations into their source code, and statistics and observations from PRODAFT’s insights into the PYSA group. A private version is available for law enforcement agencies.
Technical and statistical analysis
PRODAFT’s Threat Intelligence team worked from September 2020 to detect and gain visibility into PYSA’s ransomware infrastructure and analyzed its findings to gain insight into how the criminal operation works.
Identifying the professional development tools and methodologies, encryption, and infrastructure used by the group, and the operational mistakes they made, PRODAFT found many clues that could lead to the operators’ identities.

Unlike most highly automated threats that target many potential victims, PYSA is a highly manual ransomware, requiring operators’ personal effort that focuses exclusively on high-value targets, PYSA administrators used hidden TOR network for their operation, and they stored terabytes of victim data in Amazon AWS buckets.
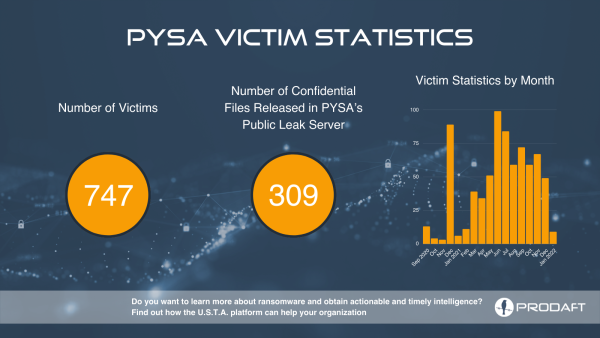
These were used to extort payments from around 747 organizations, topping out with 99 victims at the effort’s height in June 2021. Around 58% of organizations paid out to get their data back.
With four key players running PYSA, PRODAFT used new deep neural networks to drive author profiling technology to help analyze their use of language to provide further clues to their identity.
Before your business becomes a successor group’s next victim, PRODAFT provides threat intelligence to deliver actionable insights to cybersecurity professionals.
European Media Contact:
Note that a private version of this report is available for law enforcement and other agencies. Please contact [email protected] for details.
Media Contact
Company Name: PRODAFT
Contact Person: Beyza Keskin
Email: Send Email
Phone: +41225481923
Country: Switzerland
Website: https://www.prodaft.com